Remote IoT With SSH Keys On Raspberry Pi: Secure Access Guide
Are you tired of wrestling with complex SSH key management for your Raspberry Pi and IoT devices? Unlocking the power of secure, remote access doesn't have to be a headache; the right approach can make it surprisingly straightforward.
The digital landscape is evolving at a breakneck pace, and with it, the imperative for robust security measures. In the realm of Internet of Things (IoT), where devices are often deployed in remote locations and physical access is impractical, the need for secure, remote management is paramount. SSH (Secure Shell) keys have emerged as a cornerstone of this security paradigm, offering a robust mechanism to establish secure connections and manage devices from anywhere in the world. However, the default setup for SSH key management can be fragmented and complex, creating vulnerabilities that malicious actors can exploit. Unmanaged SSH keys, left to their own devices, are like unguarded doors in a digital fortress.
Fortunately, there are solutions that simplify this process, enabling secure and seamless access to your Raspberry Pi and IoT devices. The remoteIoT platform, for example, offers a streamlined approach to SSH key management. This is particularly important in todays connected world, where the potential for cyber threats is ever-present. Using SSH keys instead of passwords is a strong move towards establishing a secure environment. This method allows users to remotely control, monitor, and update devices from a centralized location.
- Movierulz 2025 Latest Telugu Tamil More Updates News
- Hdhub4u Download Stream Movies Risks Alternatives Guide
The remoteIoT platform is like a Swiss Army knife for managing IoT devices, including the Raspberry Pi. It lets developers control, monitor, and update devices from one central place, greatly simplifying what would otherwise be a time-consuming and complex process. The platform leverages SSH keys to secure communication between IoT devices and the central server. When a new device is added, it generates an SSH key pair. The public key is then uploaded to the server, while the private key is stored securely on the device.
For those new to the world of IoT and the remoteIoT platform, or anyone managing remote servers, SSH keys provide the key to secure, seamless access. This guide explores how the remoteIoT platform simplifies SSH key management for Raspberry Pi, ensuring your devices remain secure and accessible. It walks you through everything you need to know about configuring SSH keys for your Raspberry Pi using the remoteIoT platform, ensuring that the process is as straightforward as possible.
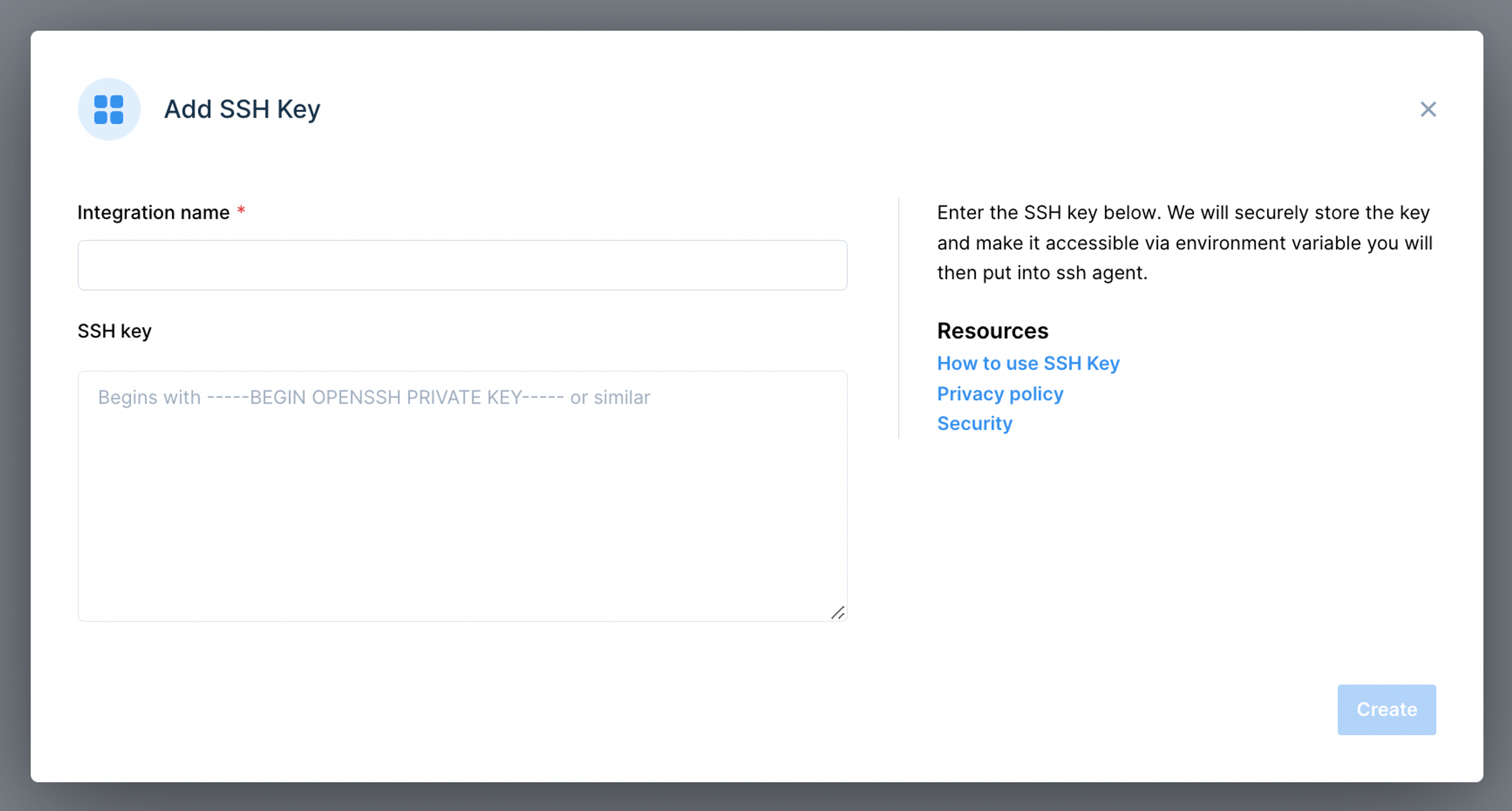
When an SSH key is set up in the remoteIoT platform, a secure channel for communication is created. This process typically involves generating a key pair on your system, copying the contents of the public key file (e.g., ~/.ssh/id_rsa.pub), and pasting it into the appropriate field on the remoteIoT dashboard. The integration of SSH keys with Raspberry Pi through this platform not only enhances security but also simplifies device management. It is a crucial step towards ensuring the security and reliability of your setup.
- Vegamovies Alternatives Streaming Guide Safe Movie Options
- Watch Movies Online Your Ultimate Guide To Streaming Alternatives
For individuals encountering issues with their remoteIoT platform SSH key not working on their Raspberry Pi, there are troubleshooting steps to follow. These include ensuring the key is properly configured, checking network connectivity, and verifying the device's SSH settings. SSH is inherently secure, but it's essential to take basic precautions. Ensure the platform can handle the growth of your IoT network as you add more devices. Centralized management of keys is a key feature. It helps in the overall process of simplifying device management.
The path to setting up a remote IoT platform with SSH keys for your Raspberry Pi involves several steps: install the necessary software on your Raspberry Pi, configure your IoT platform to accept SSH connections, and ensure all connections are properly secured. One of the most critical criteria for choosing the best remote IoT platform is ensuring it can handle the growth of your IoT network as you add more devices. This ensures the platform remains scalable and adaptable to your evolving needs.
With remoteIoT SSH key management, the user can centrally manage and discover all authentication keys and SSH login files. SSH keys offer enhanced security and simplified device management. This is particularly true when utilizing the remoteIoT platform. When it comes to managing IoT devices, this centralized approach is a considerable advantage. SSH allows users to manage these devices securely from anywhere in the world, adding to its appeal.
For those seeking a free remote IoT platform to securely manage their Raspberry Pi using SSH keys, there are several options available. Exploring these alternatives allows you to find the perfect fit for your needs without incurring additional costs. The remoteIoT platform is like the swiss army knife for managing IoT devices, including the Raspberry Pi. By incorporating SSH keys into your remote IoT platform, you're taking a significant step towards ensuring the security and reliability of your setup. SSH keys are super important because they ensure secure communication between devices. They're like the secret handshake that says, yes, I totally belong here.
By incorporating SSH keys into your remote IoT platform, you're taking a significant step towards ensuring the security and reliability of your setup. Whether you're setting up a smart home, building an IoT project, or managing remote servers, SSH keys are your golden ticket to secure, seamless access.
In the world of IoT, devices offer automation, efficiency, and convenience. However, leaving them unmonitored can open up avenues of vulnerability. Remote monitoring and alerting for Raspberry Pi and IoT devices is a must. Ssh your IoT device with the system user or ssh key based secure authentication and these standard client tools, like PuTTY. No security holes in other private client tools and protocols.
Now, imagine you can securely manage and control your Raspberry Pi devices from anywhere in the world without spending a dime. The use of SSH keys ensures a higher level of security when compared to using passwords.

Detail Author:
- Name : Mr. Lenny Hettinger
- Username : blick.jerrold
- Email : upton.glen@hotmail.com
- Birthdate : 1973-10-23
- Address : 398 Dale Highway Apt. 923 Lake Tyreebury, IA 77226-1844
- Phone : +1 (475) 322-2513
- Company : Treutel, Haag and Waters
- Job : Central Office and PBX Installers
- Bio : Sint consequatur at perspiciatis qui quas itaque rerum. Ex dolore id vitae doloribus esse deserunt. Minus aut dolorum explicabo fugiat vero. Sed suscipit excepturi veniam.
Socials
linkedin:
- url : https://linkedin.com/in/hermanb
- username : hermanb
- bio : Et quo libero eveniet ut deleniti rem.
- followers : 1786
- following : 2134
instagram:
- url : https://instagram.com/bherman
- username : bherman
- bio : Eos culpa vel nostrum aspernatur. Vero quis totam architecto nisi.
- followers : 3709
- following : 1143
twitter:
- url : https://twitter.com/beryl.herman
- username : beryl.herman
- bio : Labore est repudiandae laborum autem eum dicta nulla. Accusantium molestias eos et consequuntur.
- followers : 4542
- following : 929
facebook:
- url : https://facebook.com/hermanb
- username : hermanb
- bio : Repellendus veniam sapiente sunt.
- followers : 4194
- following : 2332
tiktok:
- url : https://tiktok.com/@berylherman
- username : berylherman
- bio : Excepturi omnis aut fugiat molestias in.
- followers : 1133
- following : 2001